Device Auth: Snooze and User Experience Improvements
Note: check snooze is only available for organizations using our Device Trust for Okta solution
In this Changelog, we’re going over two updates to our UI that streamline authentication for end users. In the first, we’ve made our “snooze button” easier to locate and use. In the second, we’ve reduced the frequency users will encounter the “warning” screen while authenticating. Both these improvements are in response to customer feedback, so thanks for sharing your experiences, and keep ‘em coming!
Snooze a single blocking Check
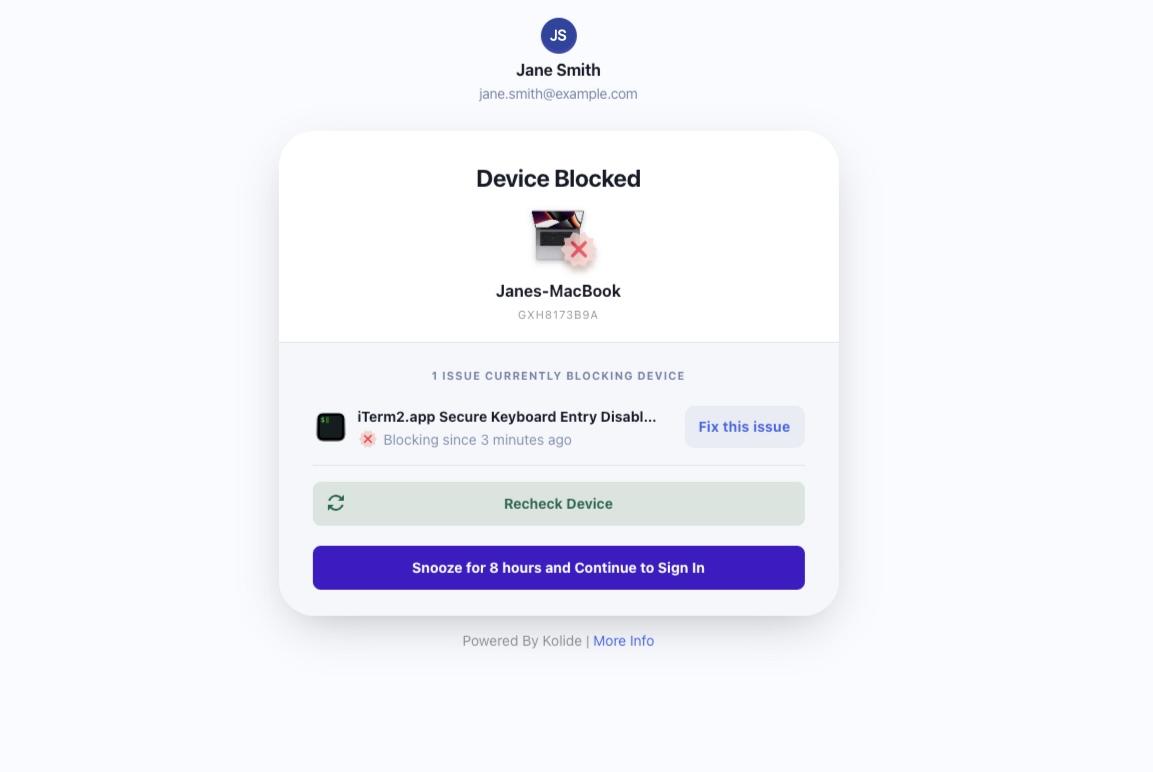
Earlier this year, we introduced snoozing for checks, allowing users to authenticate for 8 hours even if they are failing a check. (The idea being that it’s too disruptive not to give users an escape hatch if they’re running late to a meeting.) After we rolled out snoozing, we received some user feedback that the snooze button was a bit hard to find. In light of that, we’ve changed the UI to put the snooze button front-and-center when there is a single issue blocking authentication.
We only allow this snooze functionality when there is a single blocking check which is configured as snoozeable. There are two reasons we restrict snoozing to a single blocking check at a time:
- It’s bad security practice for a user to snooze multiple checks at once, and increases the likelihood the user will over-rely on the snooze feature.
- Not all blocking checks are snoozeable. Kolide admins can decide certain checks are too urgent to allow for snoozing, so we can’t bundle those with checks that can be snoozed.
Only warn a user once every 24 hours
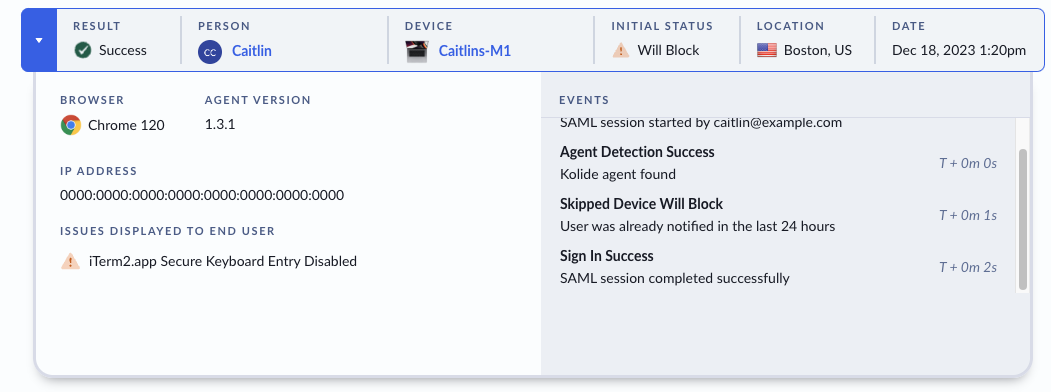
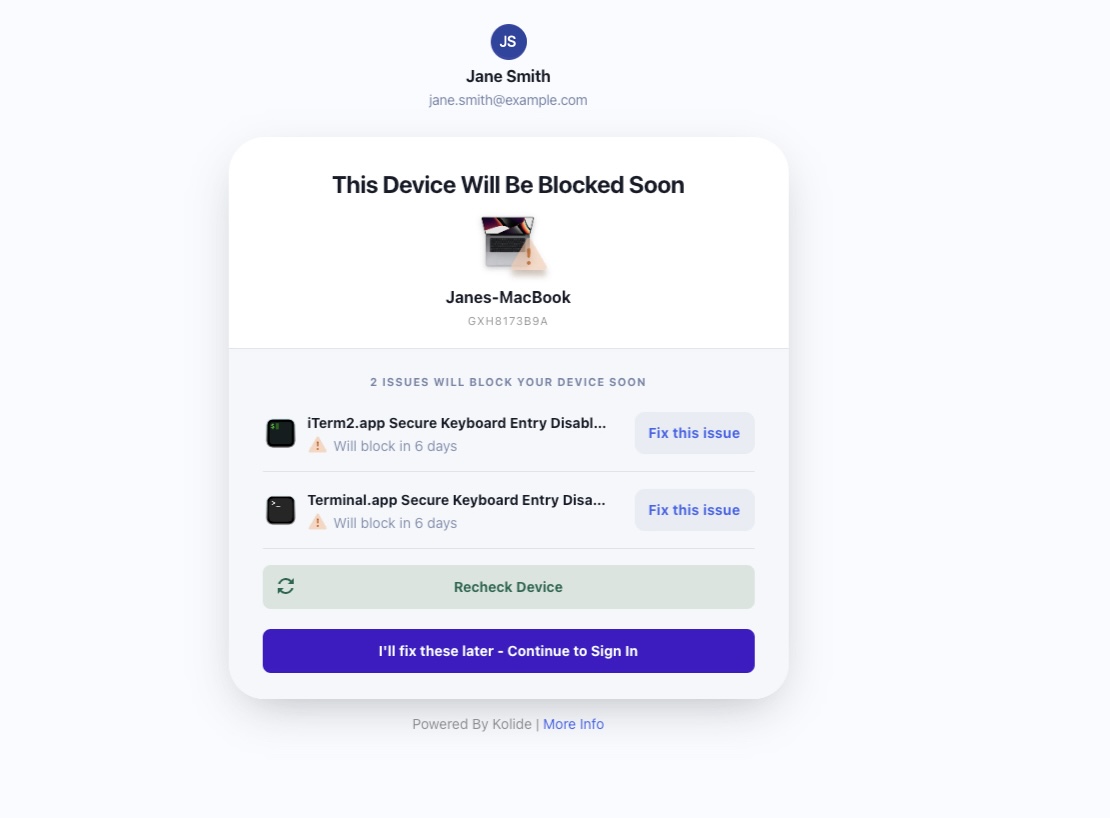
We’ve also changed how often we display our warning page in the event a user is failing a blocking check, but is still within its grace period. With this change, Kolide only warns the user of an issue once every 24 hours, instead of during every authentication flow.
In addition to this expedited authentication flow, we’ve made sure to log when a user has seen the warning screen, so that Kolide admins have full visibility into the authentication processes that make up their fleet.