Become All-Knowing
Kolide gives you accurate, valuable, and complete fleet visibility across Mac, Windows, and Linux endpoints.
Hard Questions?
Easy Answers.
Kolide can help you list Chrome Extensions across your entire fleet, automatically grouping them by their unique IDs.
Kolide automatically imports risk scores from crxcavtor, enabling you to sort extensions by their highest risk of compromise based on their permissions or the developer's reputation.
Get Started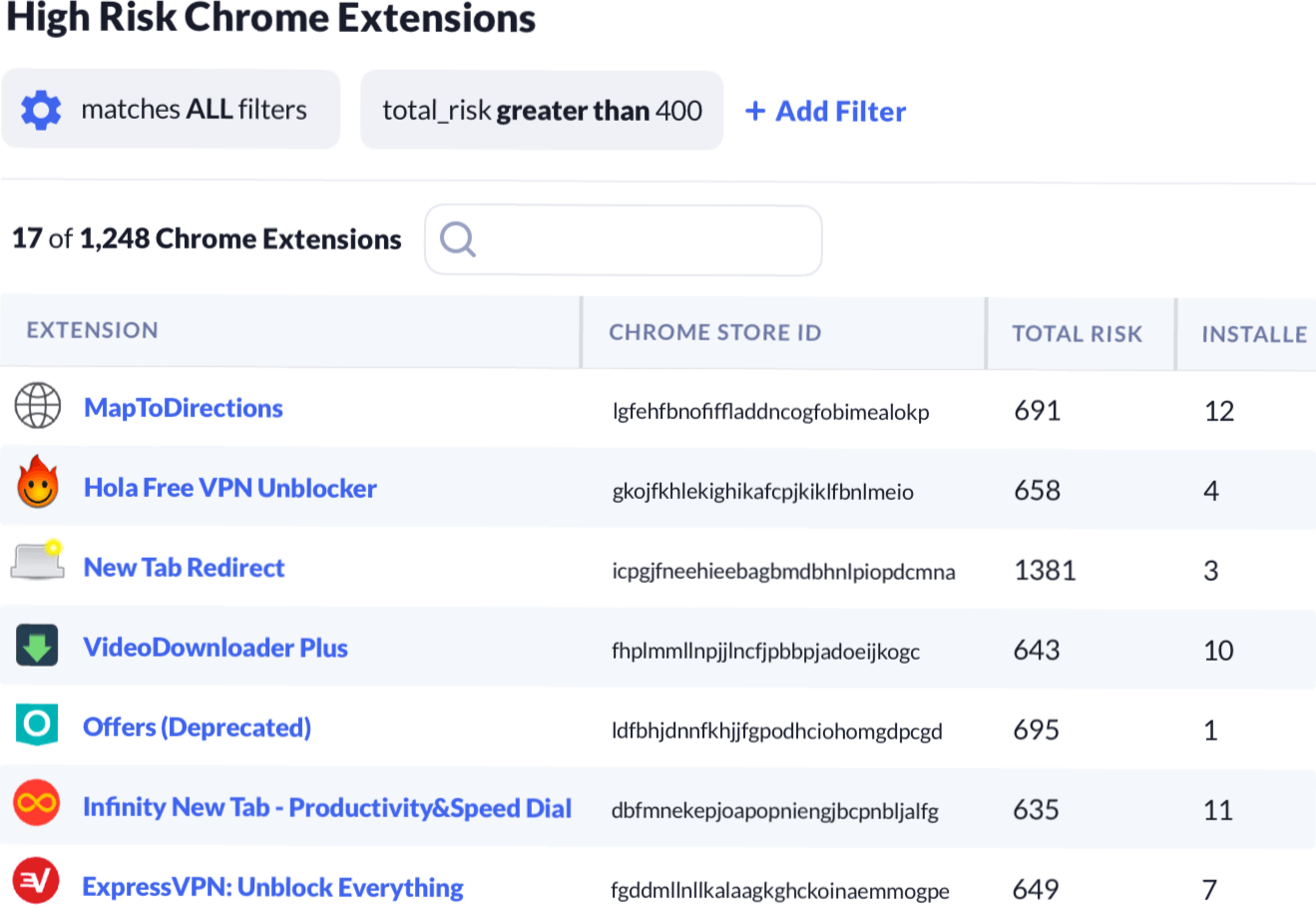
Microsoft Defender AV is built into all modern versions of Windows. Kolide can report on Defender's status, including any detected threats and its actions in response.
Reporting on threats is one of the core requirements for SOC2 and other audits.
Get Started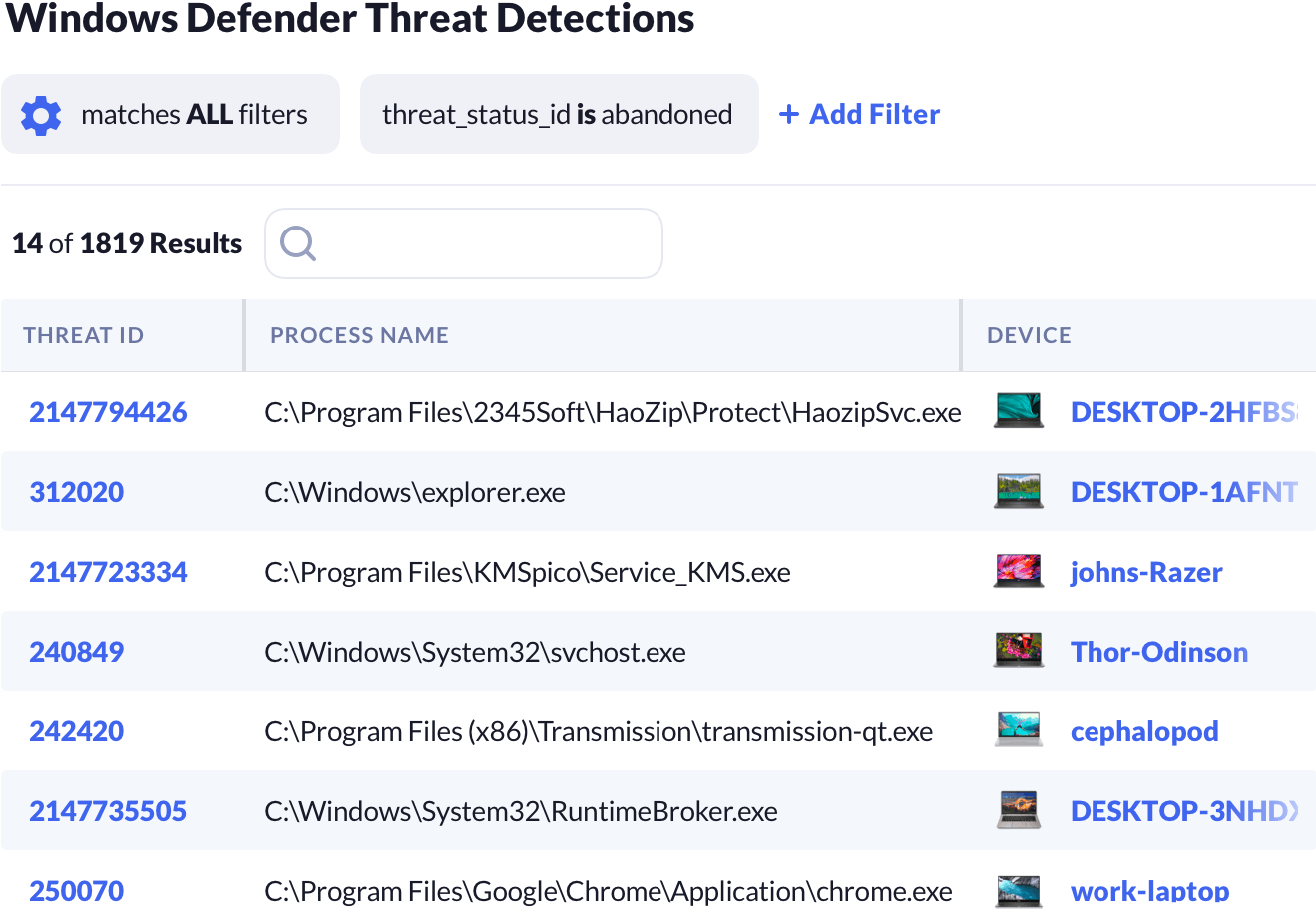
Developers keep SSH keys on their devices all the time. That's okay, as long as they are encrypted.
Using Kolide you can enumerate the user's SSH keys, get their encryption status, and even pattern match their filename to ensure you don't see things like "aws-us-east-prod".
Get Started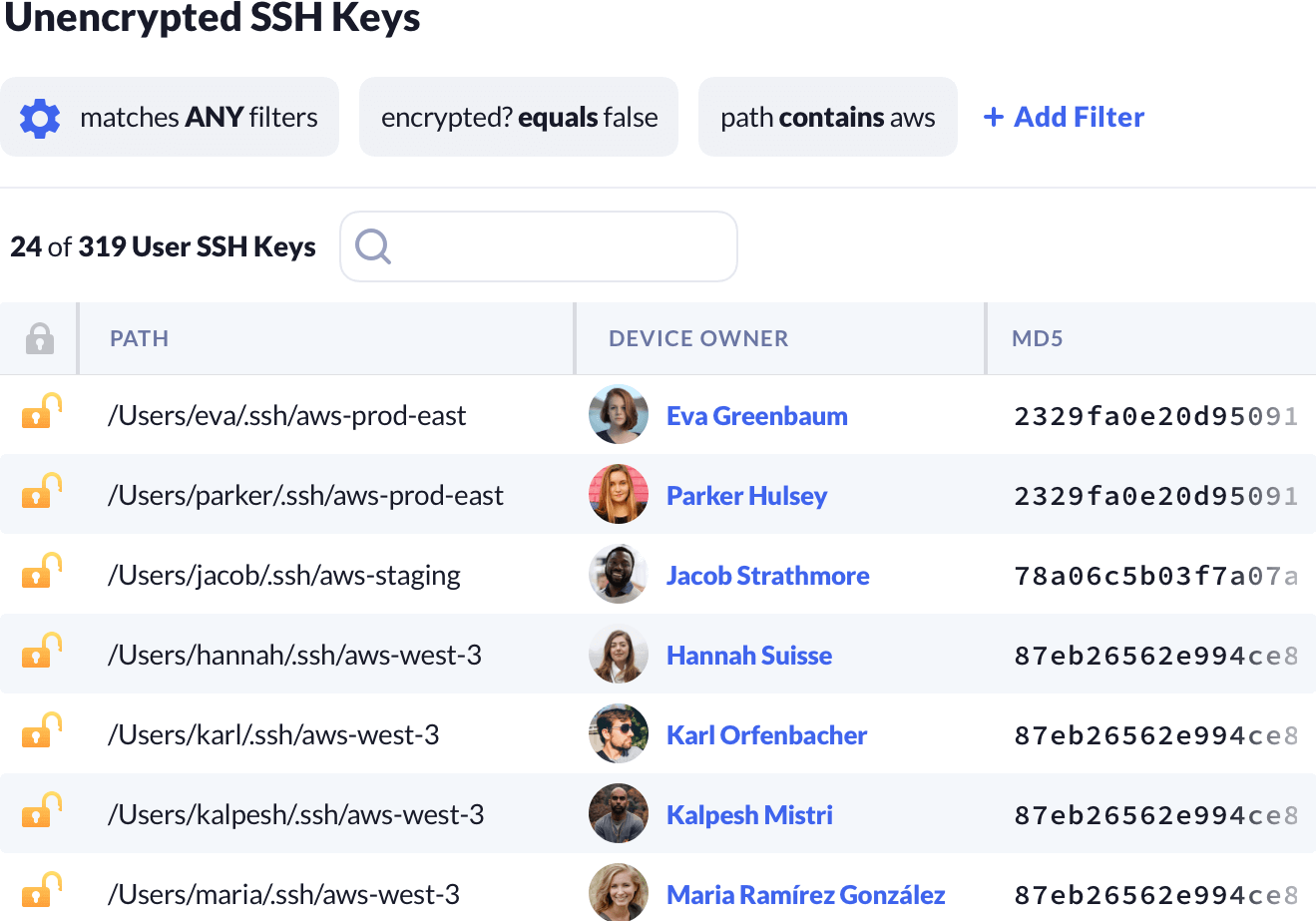
Ensure your organization uses genuine versions of Microsoft products and that the licenses match the intended usage.
Kolide can locate the Microsoft Licenses across your Windows fleet. Using this, you can identify installations of Microsoft products that may be in use with expired or non-genuine licenses.
Get Started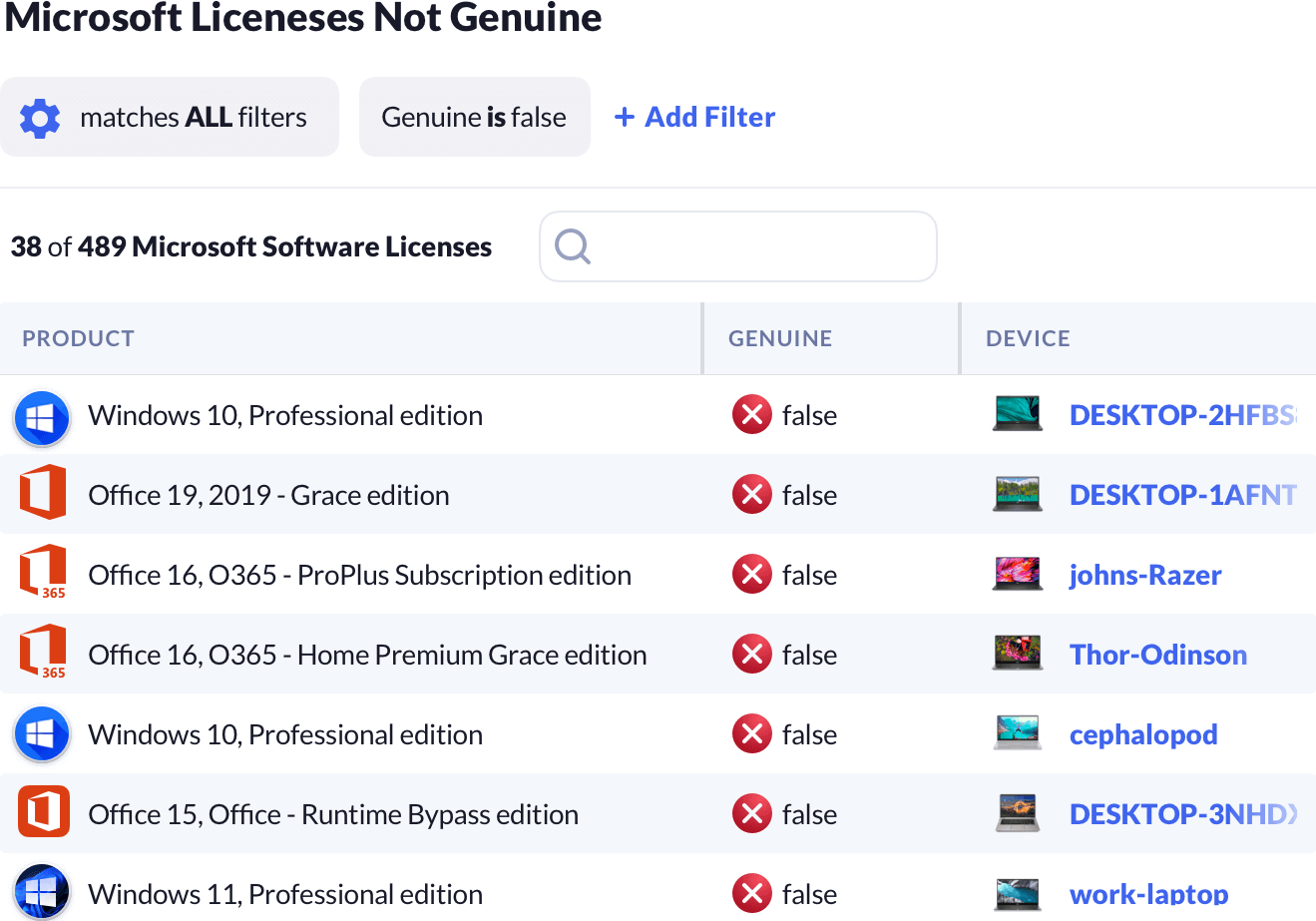
Kolide can help you and your IT team find Macs that recently crashed due to a Kernel Panic. Explore the data in inventory and you can help discover emerging problems in your fleet and the root causes that may be driving them.
Get Started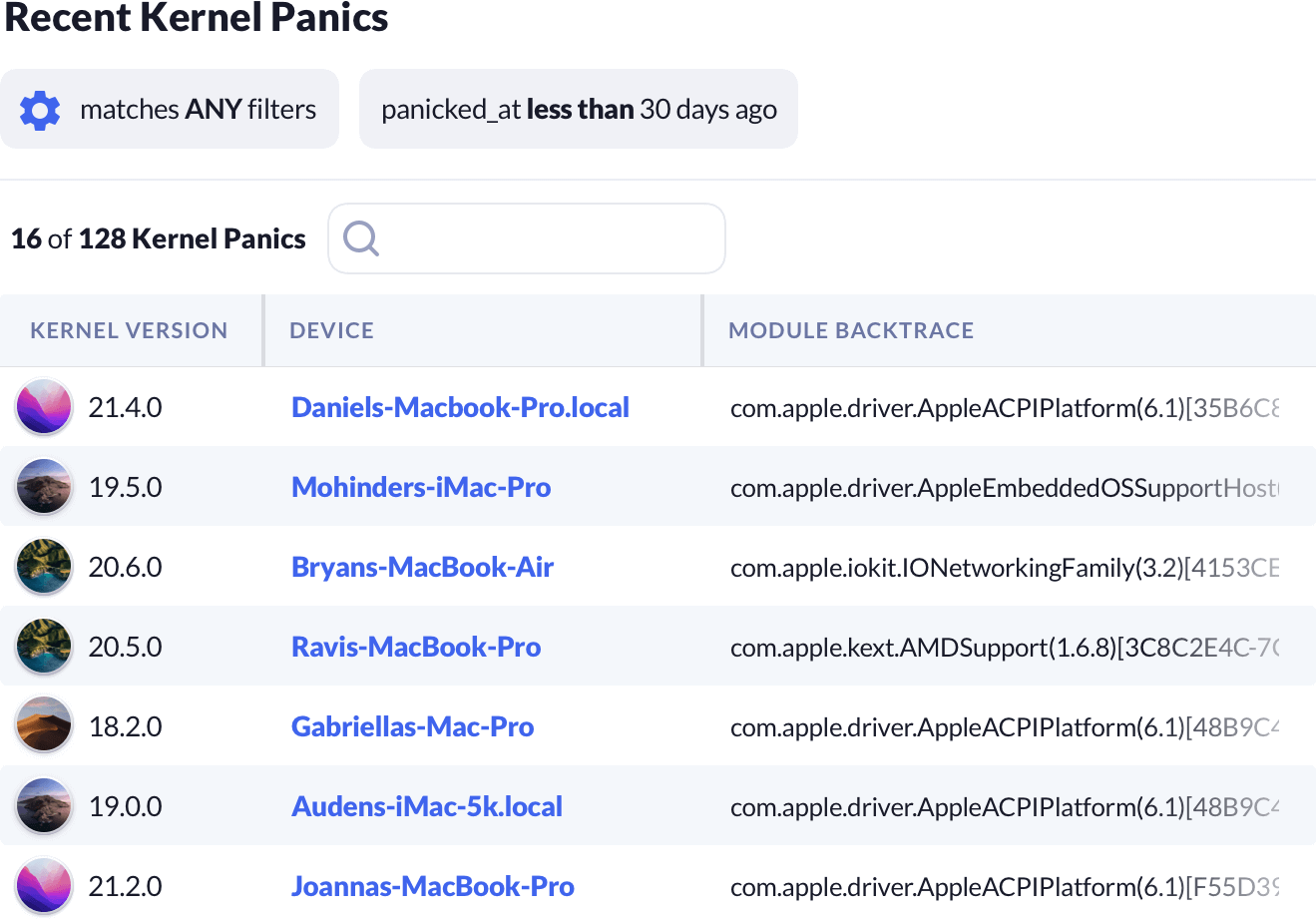
The sudoers file can offer insights into how a Mac or Linux device is used. One common issue is a user who disables sudo's built-in password protection.
Kolide's inventory can help you quickly find these insecure configurations to get your devices back on the straight and narrow.
Get Started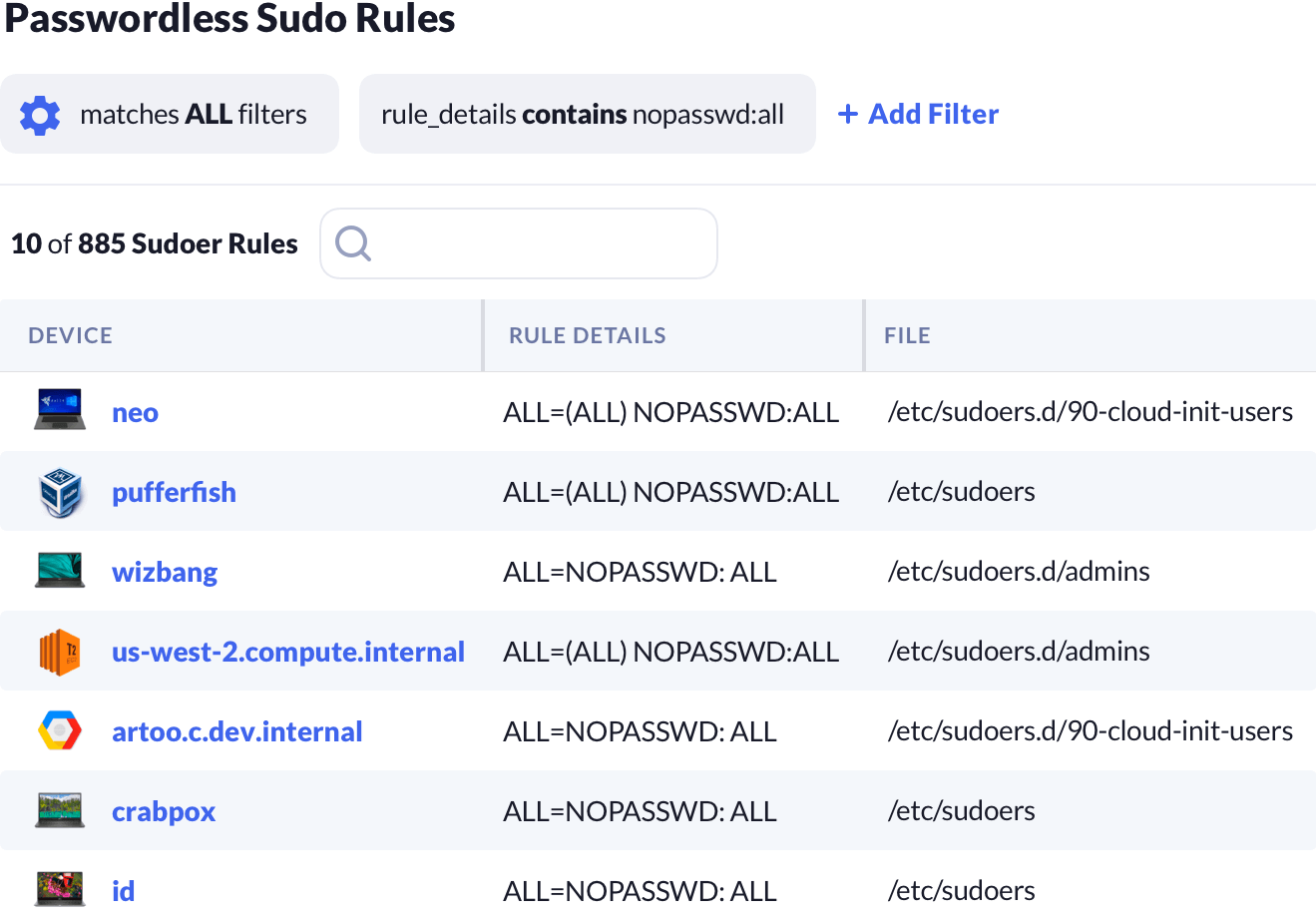
Recovering unused licenses for expensive products can be a chore, but Kolide can help.
Kolide enumerates and collects information about all installed software. With macOS apps Kolide can even return when the app was last launched by the end-user, making license recovery a snap!
Get Started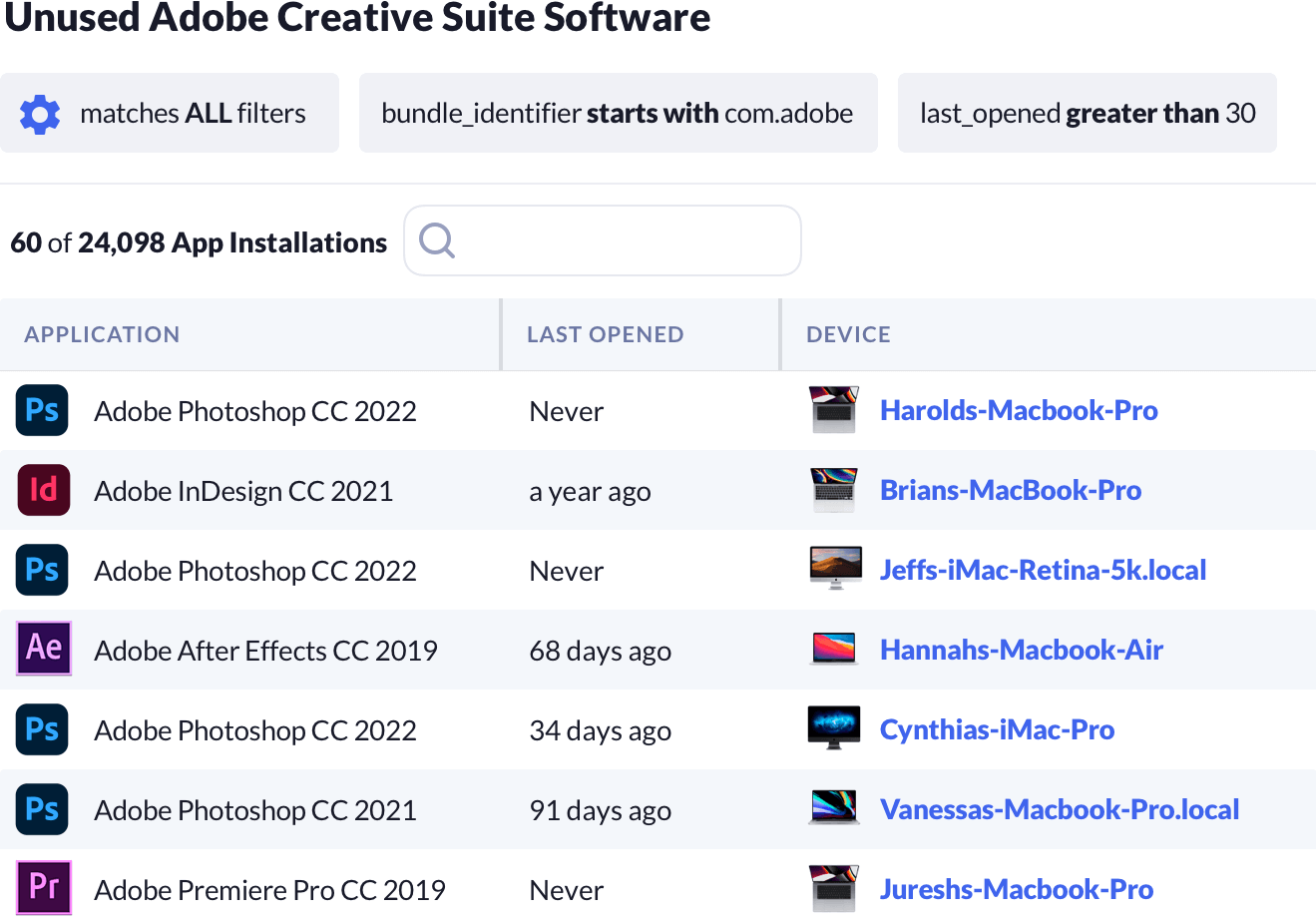
Kolide can help you identify Macs that may provide a bad experience to the end-user, like a Macbook battery that can no longer hold a charge.
Instead of waiting for end-users to reach out to you, you can proactively find them.
Get Started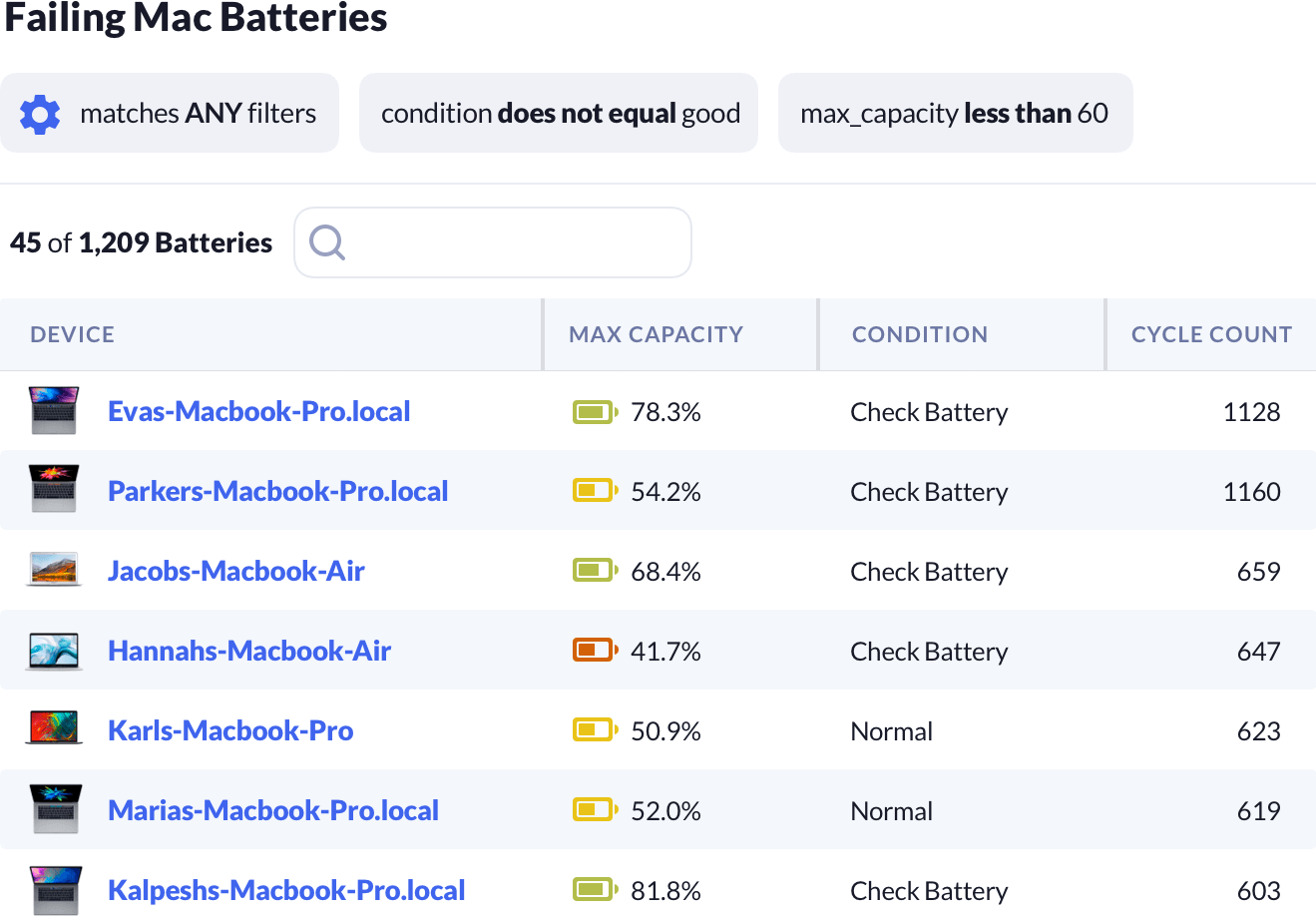
Kolide can give you insight into logical storage across all of your devices, including encryption status and the info about the underlying disk drives.
Using this, you can find devices running critically low on disk space before a device becomes inoperable.
Get Started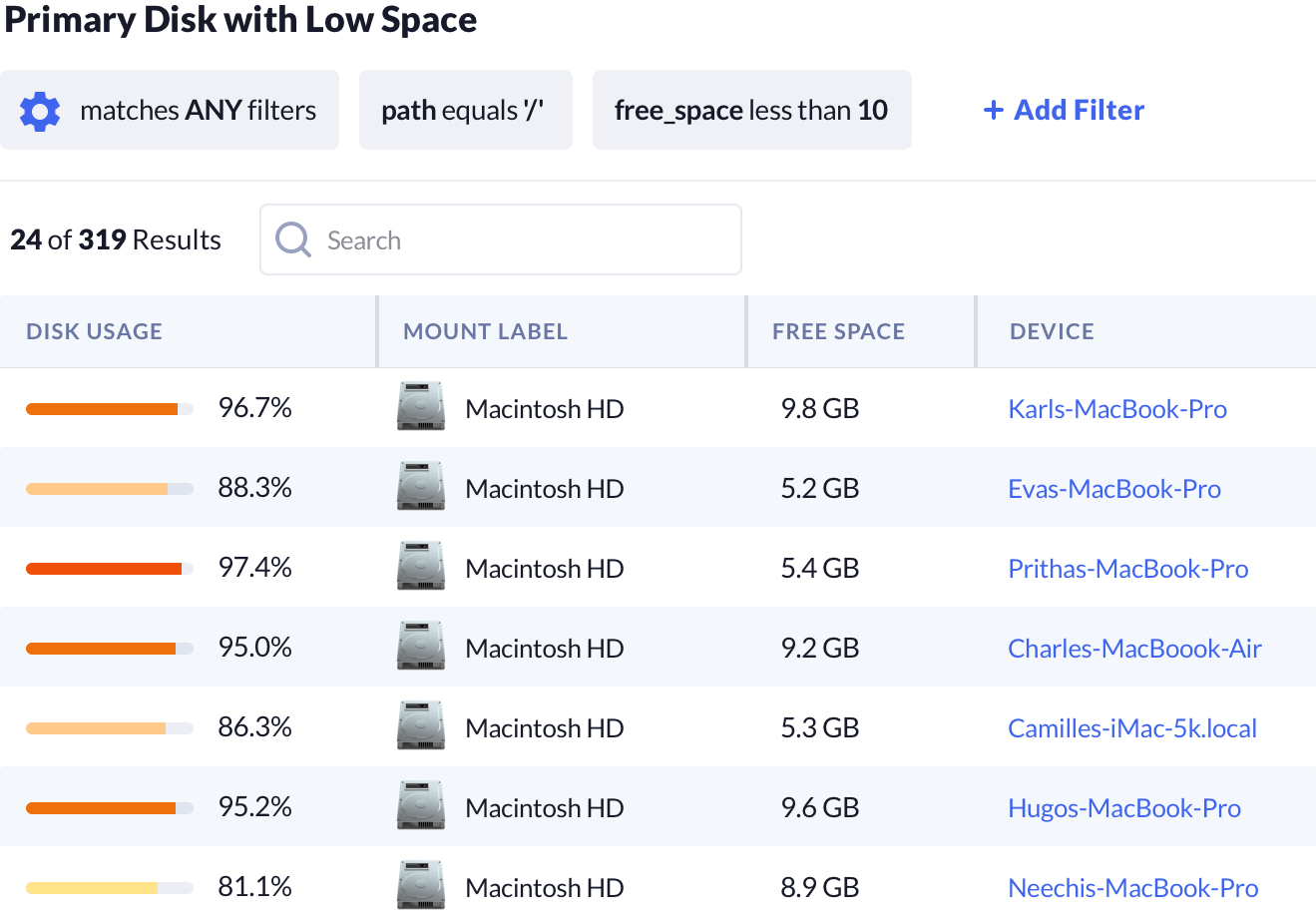
Your data.
Access it your way.
Live Query
API/Webhooks
Log Pipeline