Why We're Removing the "Unlock Mac With Apple Watch" Check
Let’s start with the tl;dr: We’re taking down our “Unlock Mac With Apple Watch” check because the feature is a little buggy on Apple’s side and we can’t always reliably detect if it’s enabled or not. Instead of fully getting rid of it, we wanted to document the query so customers can make it into a custom check if they want.
Now for the details.
What Went Wrong With This Check
When we create a new check, a lot of research and testing goes into ensuring it works on devices with different configurations and setups. This one was no different, and at first it appeared that we did everything right.
We studied Apple’s feature documentation, located the plist that stored these configurations, and tested it against devices before sending this check off to the catalog.
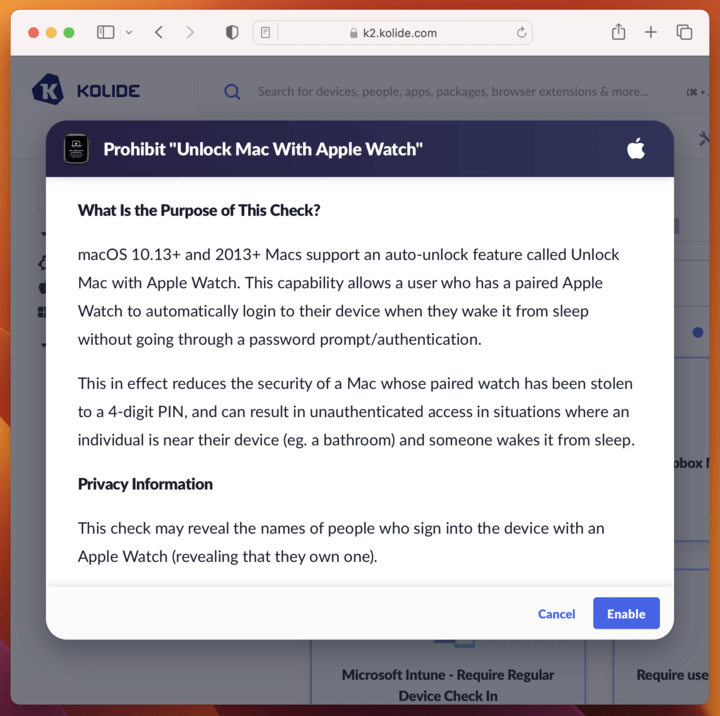
But not long after it went live, a few customers reported that they continued to fail the check even after following our fix instructions to disable the unlock Mac with Apple Watch setting.
After some deeper research and troubleshooting with our customers, we found that pairing multiple watches with a Mac or updating your watch’s OS can lead to the plist data that doesn’t match up with the Settings UI. To be more specific, the plist we pull data from would sometimes store old watches (or old data for current watches), and this old data would report that the unlock feature was still on. Meanwhile (and frustratingly for users), the settings UI would say the feature was turned off or not even show that an Apple watch was paired.
While there are some suggested fixes for this buggy behavior online, we couldn’t find anything from Apple that directly addressed this. Because we don’t have a more reliable way of detecting if this feature is enabled, and there’s also no fix publicly approved by Apple, we determined it was time our “Unlock Mac with Apple Watch” check was laid to rest.
What To Do if You Still Want To Disable “Unlock Mac with Apple Watch”
If you’re still concerned about the Apple Watch unlock feature being enabled in your fleet, fear not! We’re sharing our SQL query so you can recreate it in the custom check editor. (If this is your first run-in with our editor, you can find a guided tour in this blog post.)
Here’s where we have to give our disclaimer. We decided to remove this check from our catalog because the bug was common enough that we didn’t feel confident in its accuracy. Depending on the size of your Mac fleet and who uses this feature, you may only run into this problem a few times or not at all. Be aware that if a device continues to fail even after this setting has been turned off, it’s likely caused by this bug.
The suggested fixes we found online were not backed by Apple, so we highly recommend you contact Apple directly to resolve these issues. Or, if you’re not noticing odd behavior with the Apple Watch unlock feature and it appears to be just a reporting problem, your staff can request an exemption directly within Kolide.
In conclusion: it’s never fun to backtrack on our own work, but we wanted to be transparent about why we’re doing it. Naturally, we’ll also keep you posted if we’re able to put the check back up. The best case scenario is that the underlying plist issue will eventually be fixed and we’ll get another bite at…the Apple.
WITH
_liu AS (
SELECT
user AS username,
IIF(type = 'user', TRUE, FALSE) AS logged_in,
MAX(CASE WHEN tty = 'console' AND type = 'user' THEN TRUE ELSE FALSE END) AS desktop_session
FROM logged_in_users
GROUP BY username
),
_human_users AS (
SELECT uid, username, directory, shell, uuid
FROM users
WHERE
SUBSTR(uuid, 1, 8) != 'FFFFEEEE'
AND shell NOT IN (
'/sbin/nologin',
'/usr/bin/false'
)
AND username != '_mbsetupuser'
ORDER BY uid
LIMIT 50
),
merge_user_data AS (
SELECT
uid, username, directory, shell, uuid,
IIF(logged_in ISNULL, FALSE, logged_in) AS logged_in,
IIF(desktop_session ISNULL, FALSE, desktop_session) AS desktop_session
FROM _human_users LEFT JOIN _liu USING(username)
),
auto_unlock AS (
SELECT
mud.*,
MAX(CASE WHEN key = 'Pairing ID' THEN 'true' ELSE 'false' END) AS pairing_set_present
FROM merge_user_data mud
LEFT JOIN kolide_plist ON path = directory || '/Library/Sharing/AutoUnlock/pairing-records.plist'
GROUP BY username
),
failure_logic AS (
SELECT username, logged_in, desktop_session, pairing_set_present,
CASE
WHEN pairing_set_present = 'true' THEN 'FAIL'
WHEN pairing_set_present = 'false' THEN 'PASS'
ELSE 'UNKNOWN'
END AS KOLIDE_CHECK_STATUS
FROM auto_unlock
)
SELECT * FROM failure_logic;
Create your own Unlock Mac With Apple Watch using this query in our custom check editor.