Our New CrowdStrike Falcon Check
CrowdStrike Falcon is the most widely used EDR solution globally, making it unsurprising that many of Kolide’s customers depend on it as their primary means of defense against sophisticated threats.
Given Falcon’s significance in our customers’ strategies, they naturally want to use Kolide Device Trust to ensure that only known and trusted devices with CrowdStrike Falcon installed, running, and registered can access their most sensitive apps.
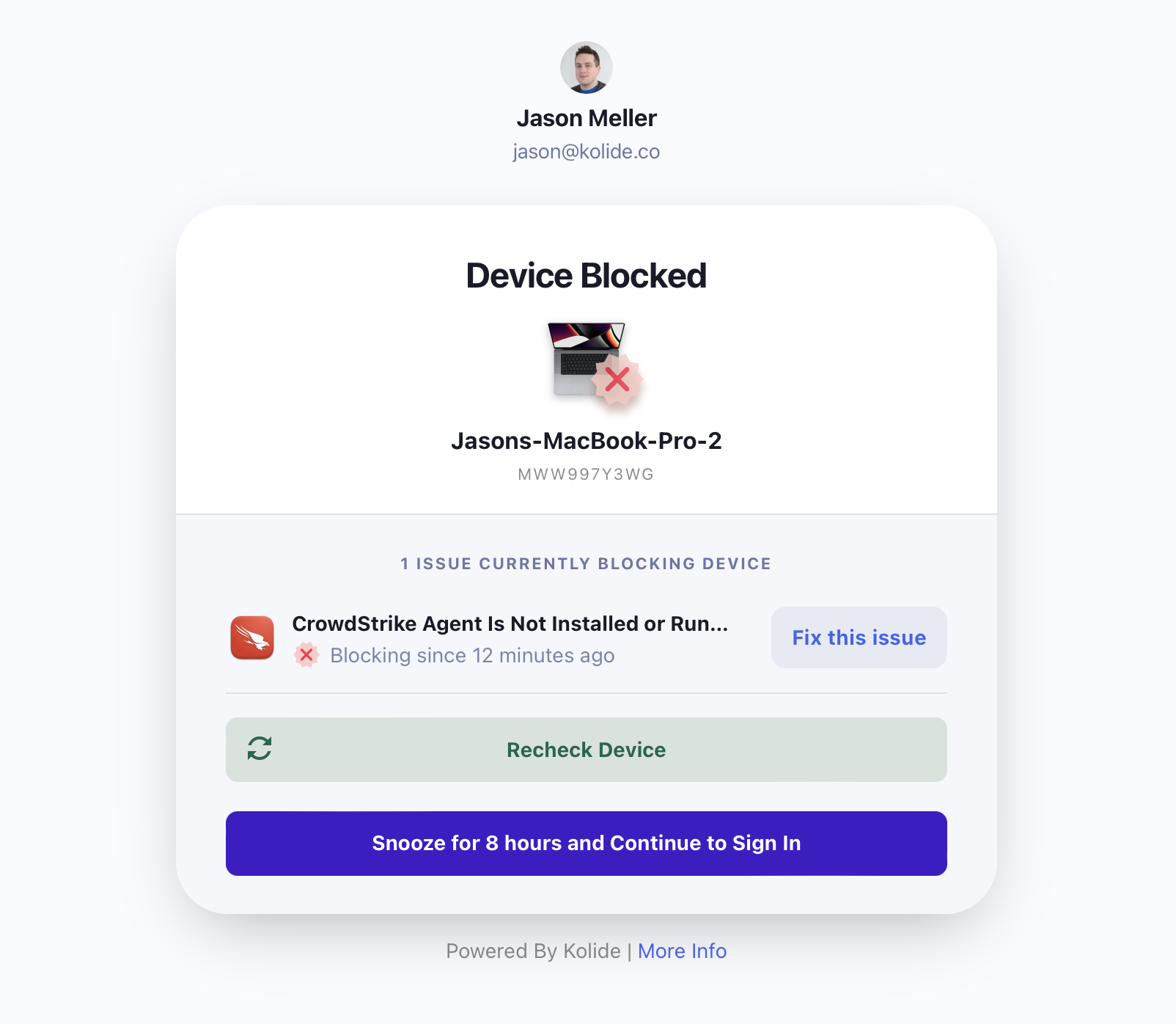
Over the past few months, we have enhanced our CrowdStrike Falcon Check
with new agent capabilities that enable Kolide to directly interact with the
falconctl utility. In this Changelog Entry, I’d like to outline its
features:
Checks for Each Platform
Kolide now offers three separate checks for each platform that CrowdStrike Falcon supports: macOS, Windows, and Linux.

Each check has slightly different capabilities based on the unique features Falcon offers within each platform. Across all three platforms, Kolide can determine if CrowdStrike is both installed and running by ensuring that:
- The required System Extensions are active (macOS)
- The required Services are running (Windows)
- The required systemd units are active (Linux)
Kolide will also collect the version of the running Falcon agent each time it performs the check.
Verifying Client ID
A CrowdStrike Falcon Client ID, often referred to as a CID, is a unique identifier associated with a customer’s instance of the CrowdStrike Falcon platform. This identifier links the deployed Falcon agents to the customer’s specific Falcon environment in the cloud. When installing a Falcon agent on a device, you must provide this CID to ensure that the agent communicates correctly with the CrowdStrike cloud, allowing threat data to be sent to and from the cloud for analysis, protection, and response actions based on the customer’s configuration and subscriptions.
Since the CID is crucial for the operational effectiveness of the CrowdStrike Falcon platform within an organization, Kolide now supports checking that the Falcon agent is both registered to at least one CID and that it matches the expected value.
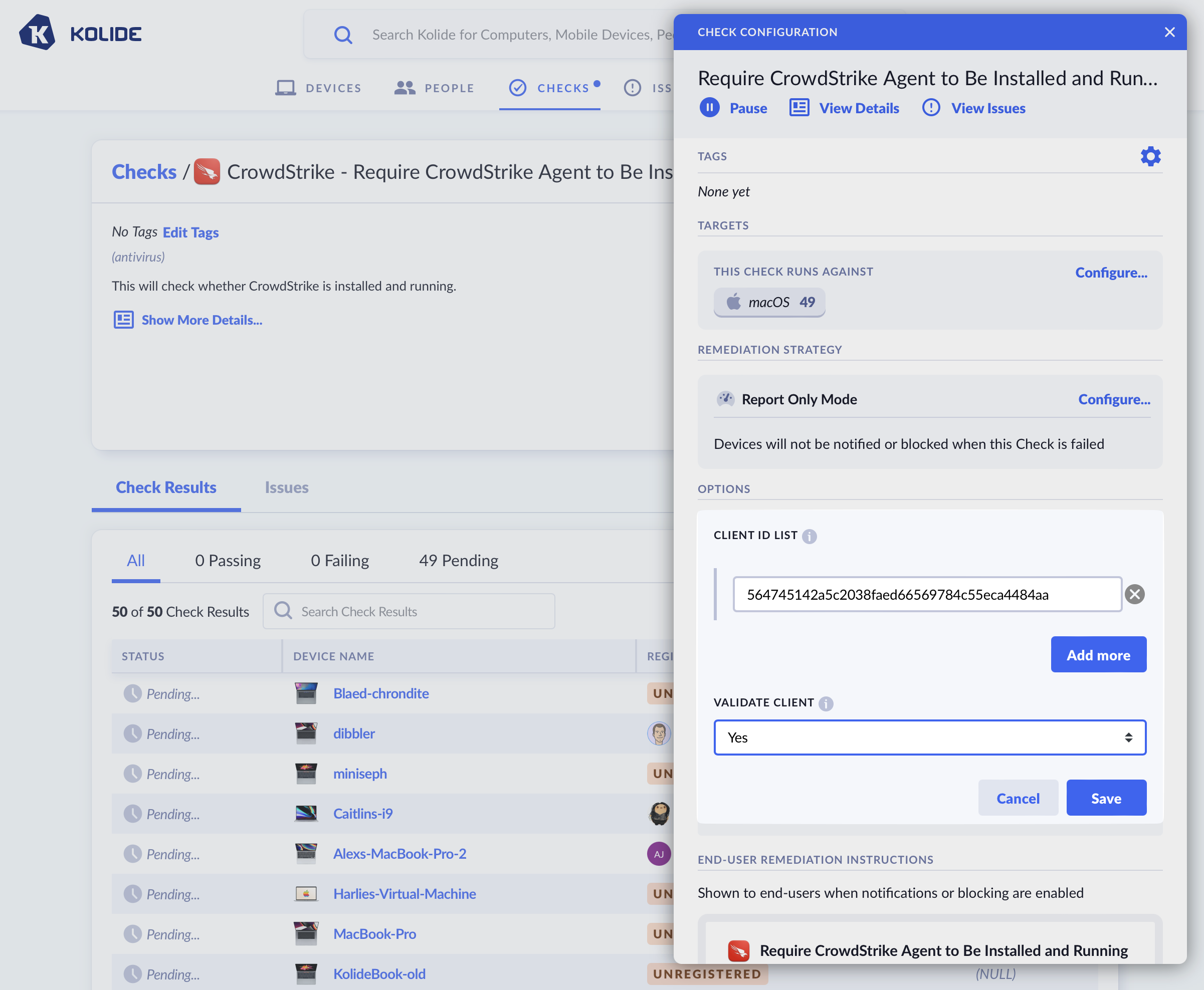
If a Falcon Agent isn’t registered, end-users will be prompted to configure it using custom remediation instructions for their specific platform. Below is an example for macOS.
The CrowdStrike Falcon Agent Is Not Configured.
Your installation of the CrowdStrike Falcon Agent has not been configured with your organization’s CID (Client ID).
If you are unsure of your organization’s CID, then you’ll need to contact your IT support team for assistance.
To set the CID on the sensor, follow the steps below, substituting
<CID>with your organization’s CID.
- Open a terminal window on your device.
- Type in the following command:
sudo /Applications/Falcon.app/Contents/Resources/falconctl license <CID>, then press enter.If the command runs successfully, you will be prompted to enable Notifications for the sensor, and see the following message in your terminal: “Licensed Falcon sensor with customer ID
”.
Verifying Agent Is Not in Reduced Functionality Mode
On Linux, Kolide can ensure that CrowdStrike Falcon is not running in Reduced Functionality Mode (RFM). This mode can be activated when the device’s Linux kernel is not supported by CrowdStrike, which may occur after an update.
You can run the following command in a terminal to verify the RFM status:
/opt/CrowdStrike/falconctl -g --rfm-state
While the Windows Falcon Agent also has the concept of RFM, it doesn’t imply the same level of reduced functionality. On Linux, if Falcon is in RFM, the device is not meaningfully protected and, in some cases, only SensorHeartbeat events may be sent back to the CrowdStrike Cloud.
Kolide’s CrowdStrike Falcon Check can now detect when the Falcon agent enters this state and, with the appropriate option set, can make the absence of this state a passing requirement.
If this occurs, Kolide’s remediation instructions will advise the user to contact IT.
The CrowdStrike Falcon Agent Is Running In Reduced Functionality Mode. CrowdStrike sensors in RFM (Reduced Functionality Mode) do very little, due to their strong dependency on the device’s kernel.
To remediate the sensor running in RFM, it will require matching your device’s kernel to a supported version of the sensor.
This means either installing another version of the sensor, or changing your device’s kernel to support the installed sensor.
We recommend contacting your IT support team for assistance with returning a sensor from RFM to full functionality.
CrowdStrike advises against allowing current sensors to enter RFM by recommending the deactivation of automatic kernel updates and endorsing kernel upgrades only when they are compatible with the Falcon sensor. It is recommended to refer to your distribution’s support guides for instructions on how to maintain the current kernel fixed or set up routine updates without altering the existing kernel.
Enhancing Device Security with Kolide’s CrowdStrike Falcon Check
Kolide’s enhanced CrowdStrike Falcon Check represents a significant advancement in ensuring the security and operational integrity of devices protected by CrowdStrike Falcon. By leveraging new agent capabilities, Kolide offers comprehensive checks across macOS, Windows, and Linux platforms, ensuring that CrowdStrike Falcon is correctly installed, running, and registered with the correct Client ID. Furthermore, Kolide’s ability to detect whether the Falcon agent is operating in Reduced Functionality Mode (RFM) adds an essential layer of security by addressing potential vulnerabilities that could compromise device protection.
By facilitating easy verification and remediation processes, Kolide helps ensure that only known and trusted devices can access sensitive applications, thereby reinforcing the security infrastructure of its customers.
As threats continue to evolve, tools like Kolide’s CrowdStrike Falcon Check will be pivotal in enabling organizations to stay ahead of potential security breaches, ensuring continuous protection and peace of mind for both IT teams and end-users.