Log Pipeline - Splunk HEC Support Now Available
Earlier this year, we launched our Log Pipeline; a feature that allows you to tap into the full benefit of osquery—the core component of Kolide’s open-source agent.
The Log Pipeline allows your Kolide team members to create a custom osquery schedule—or use the great queries we already run today to populate Inventory—and send the resulting logs to one or many supported Log Destinations.
Customers are already using the Log Pipeline to:
- Perform File Integrity Monitoring on Windows, Linux, and Macs
- Collect timestamped data from one of many of osquery’s event-style tables (ex:
process_events,process_file_events,hardware_events,syslog_events, etc.) - Collect a rich history of device state that can be imported and searched in a SIEM or Log aggregation tool.
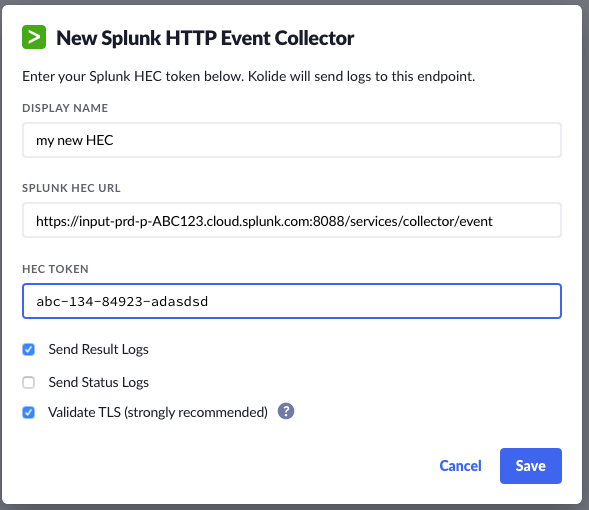
Due to popular demand, we are excited to announce the availability of new Log destination—the Splunk HTTP Event Collector (HEC).
To learn more about the Splunk HTTP Event Collector (HEC) and how you can add as a new destination to your existing Log Pipeline, please visit our help article.
As always, please let us know if you have feedback or questions about this new destination or other improvements you’d like to see in the Log Pipeline feature.




