Zoom Webcam Hijacking — Are Your Users Vulnerable?
On July 8th, Jonathan Leitschuh published a vulnerability report for the popular teleconferencing application Zoom:
“This vulnerability allows any website to forcibly join a user to a Zoom call, with their video camera activated, without the user’s permission.”
With ¾ of a million companies relying on Zoom to conduct video meetings, the number of vulnerable individuals is staggering. If your organization currently uses Zoom, you may be stuck wondering which of your users are affected.
Thankfully, Kolide provides a clear path towards identifying unsafely configured devices and remediating the issue.
Update 7/9/19 5:30PM:
The Zoom team pushed changes to the client (in response to overwhelming pressure from the community) which removes the local webserver feature of the Zoom app and permits normal uninstallation:
Current Release
July 9, 2019 Version 4.4.53932.0709 Download Type: Prompted Download here: Download Center
General Features
Option to uninstall Zoom Zoom users can now uninstall the Zoom application and all of its components through the settings menu.
Resolved Issues
Removal of the local web server Zoom will be discontinuing the use of a local web server on Mac and will be completely removed from the Zoom installation.
What do I need to look for?
There are two main components of this vulnerability:
A persistent listening port that allows a meeting to be auto-joined by serving a malicious URL in an i-frame.
Your web-camera is activated by default when joining the meeting.
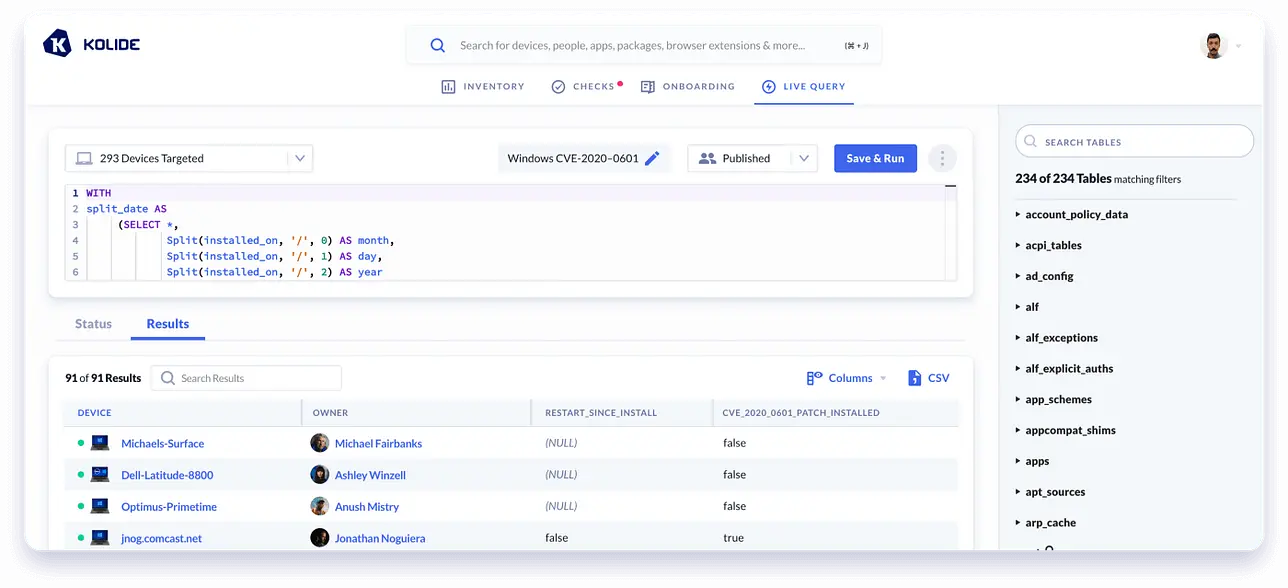
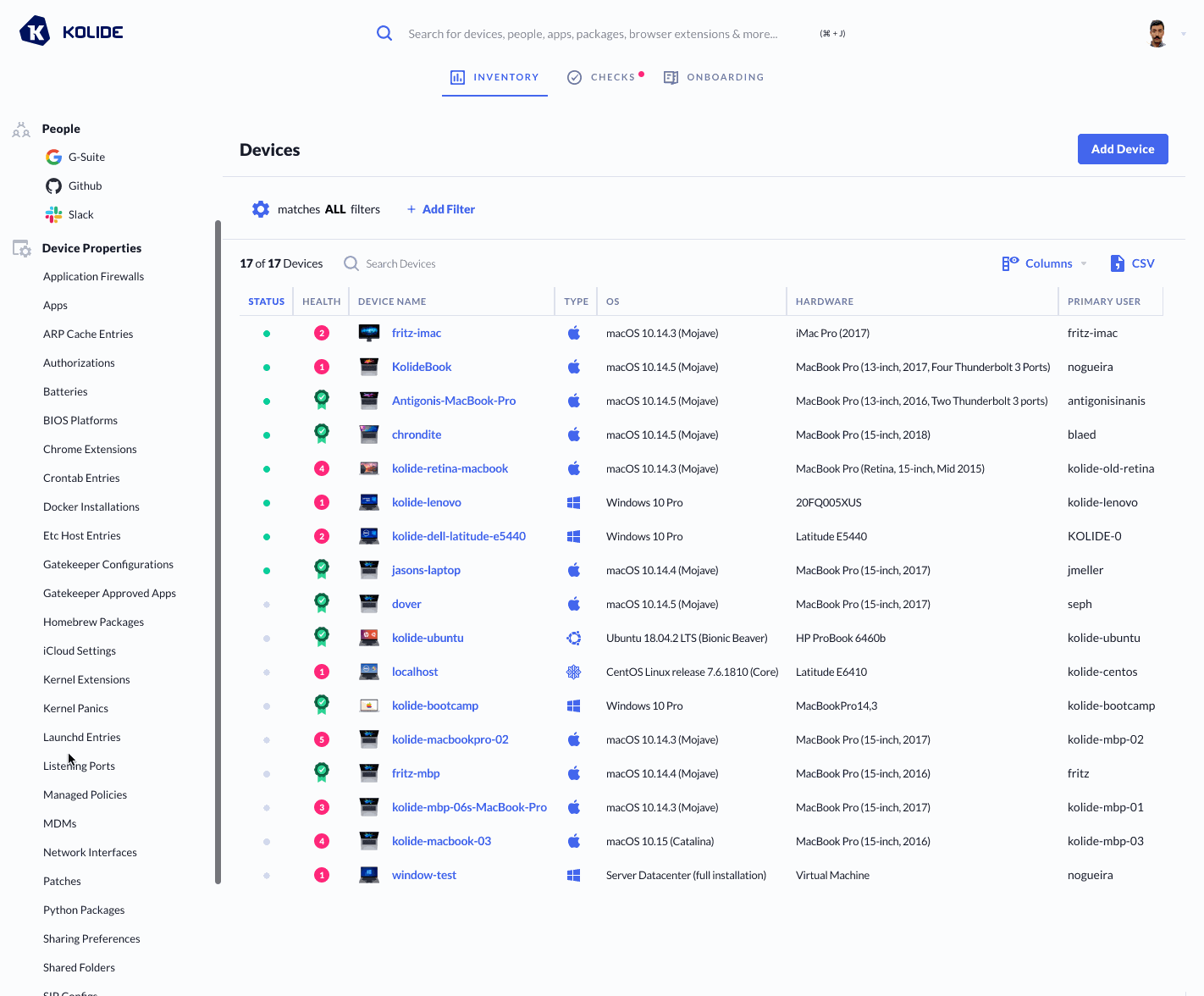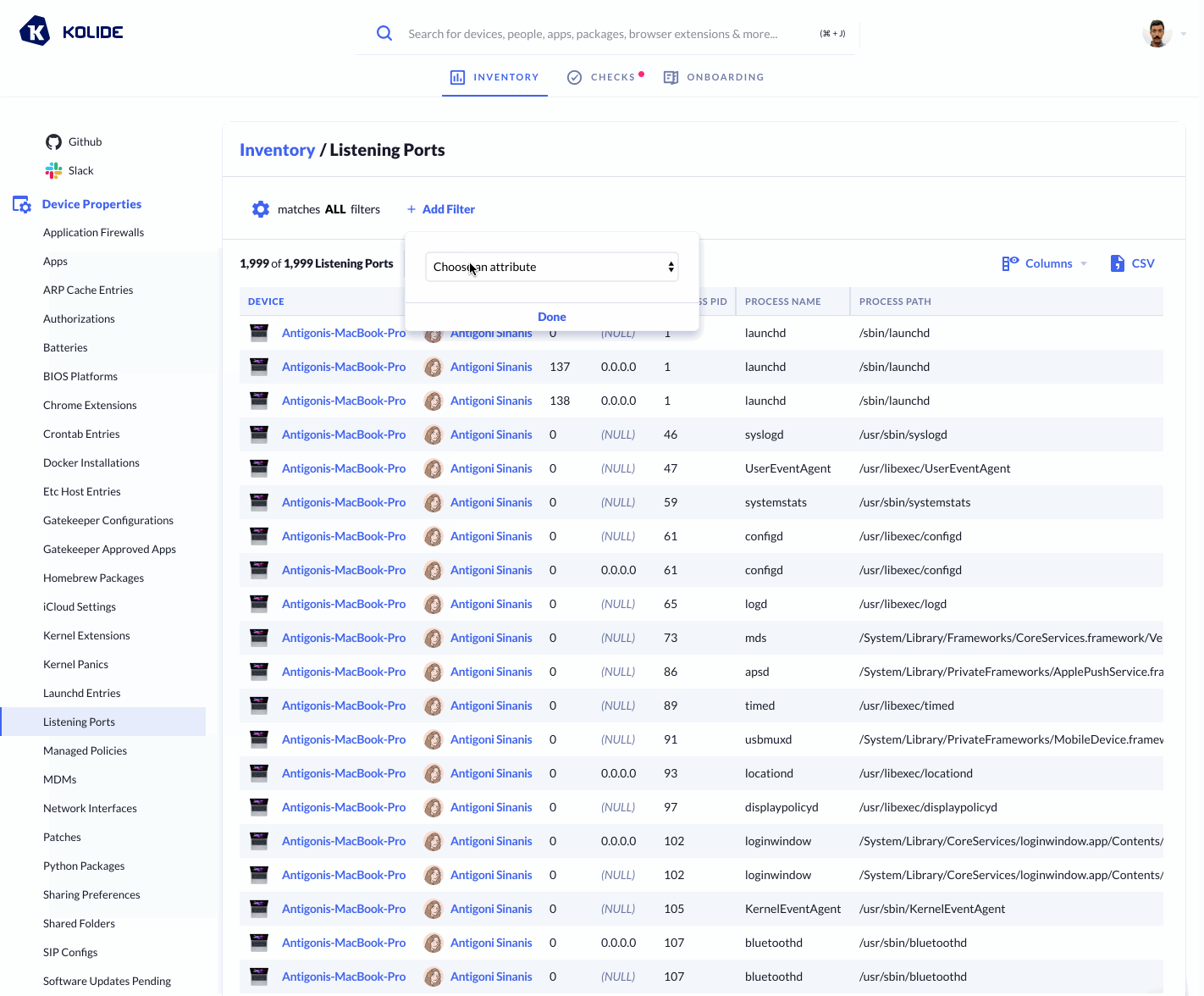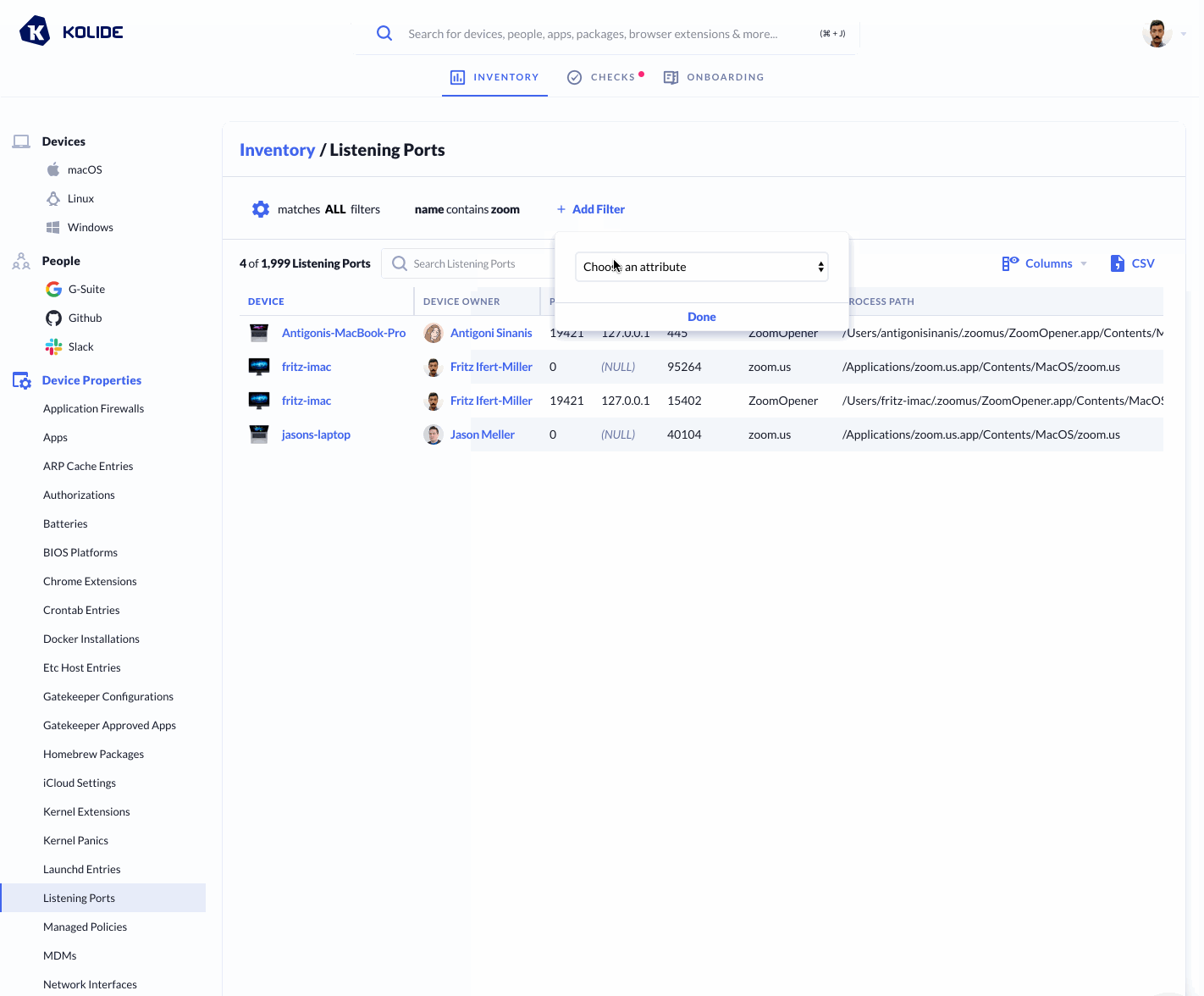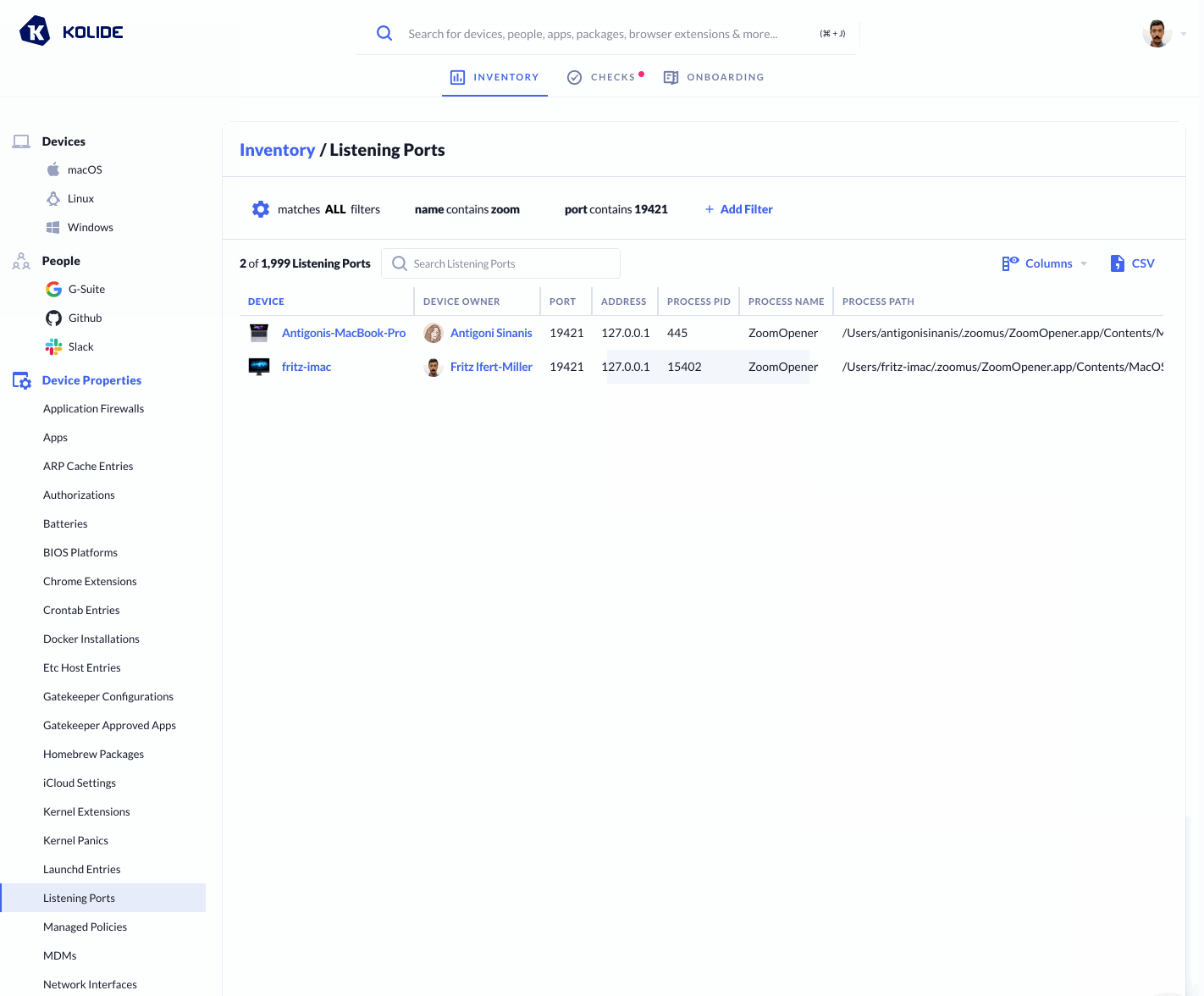
Kolide conveniently provides a list of all listening ports and the respective processes that are utilizing them via our Inventory feature.
Below we can see a gif filtering down to check whether the Zoom process is
listening on port 19421, and we see it is on 2 of our devices:
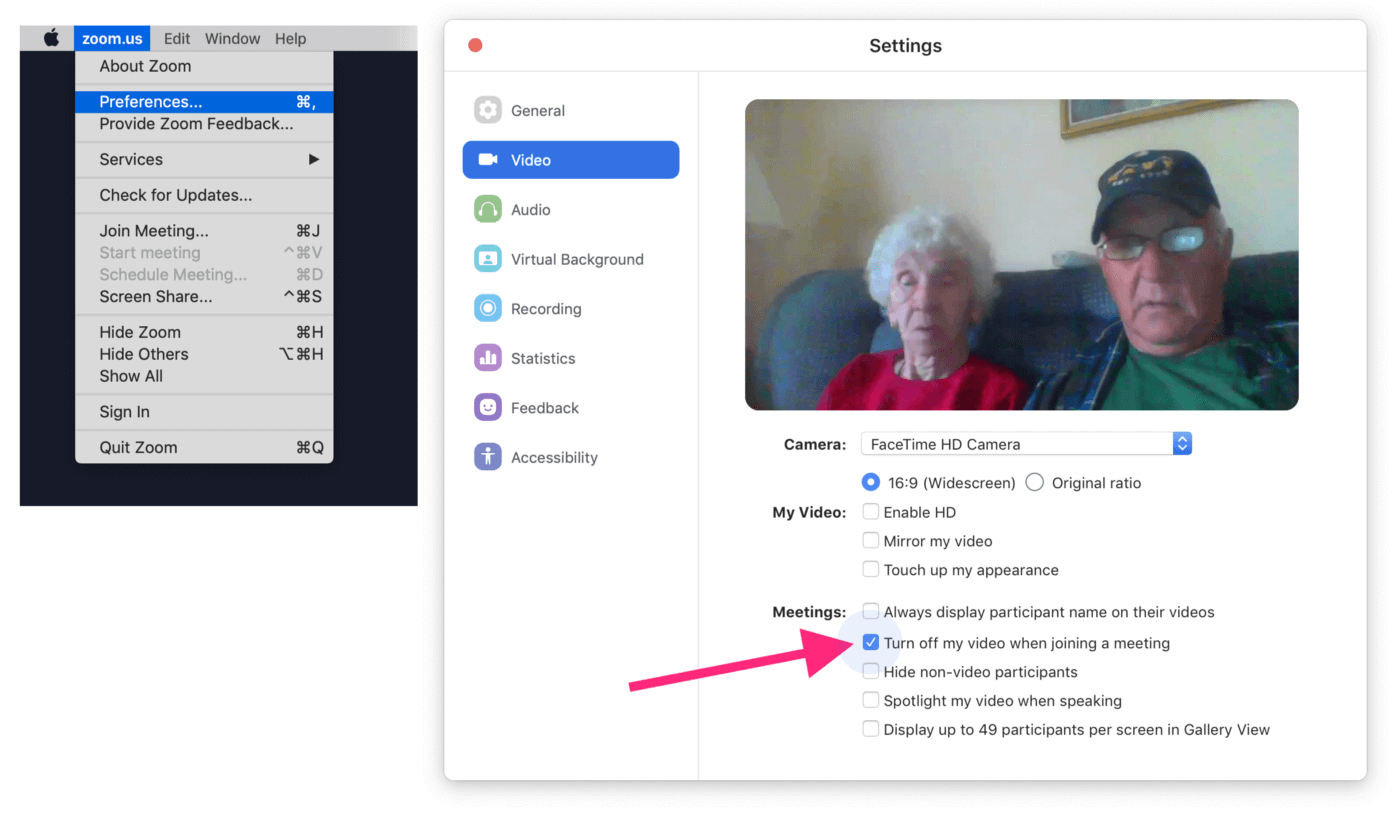
Next, we can check for who has their camera disabled by default.
This setting can be configured in Zoom by following these steps:
- Click on Preferences
- Go to the Video Tab
- Ensure the checkbox: “Turn off my video when joining a meeting” is checked.
How is this preference value stored?
Zoom stores this and several other preferences in a sqlite DB located at:
~/Library/Application Support/zoom.us/data/zoomus.db
There is a value in the zoom_kv table which encodes some of the various
preference settings as a string:
sqlite3 ~/Library/Application\ Support/zoom.us/data/zoomus.db "SELECT value from zoom_kv where key = 'com.zoom.pt.settings.general';"
304878224
That string can be converted from base-10 to binary:
100 1 0001011000001001010010000
If you count to the 26th position starting from the right
1 = Disable Camera by Default
0 = Enable Camera by Default
Kolide looks for this setting as part of our Vulnerable Apps Check. When it finds devices that do not have the checkbox checked, our Device Trust solution automatically notifies end users with information about the vulnerability, and instructions on how to protect themselves from being a victim of the exploit.