Apple's Passkeys Are a Big Step to a Passwordless Future
At WWDC21, Apple announced an ambitious plan to do away with passwords once and for all, replacing them with secure-by-design credentials called passkeys. The feature preview started by making the familiar case against passwords: they’re vulnerable to phishing and credential stuffing attacks, protecting them is difficult, and people are notoriously bad at making them strong and unique.
In response to the problems with passwords, Apple created* passkeys, with the promise of “amazing security” combined with unparalleled usability.
Apple first made passkeys available in iOS 15 and macOS Monterey for developer testing, but they’ll launch for the general public in iOS 16, iPad OS 16, and macOS Ventura. There are plenty of places you can find a short summary of the new security changes or thorough explanation of passkey cryptography. But I want to focus on the real-world ramifications of passkeys for you–both the end users and the IT admins who manage device security–and identify what you need to do to prepare for passkeys.
Actually, there’s a little more to it than that, as we explain in the next section.
Passkeys Aren’t Just for Apple
To grasp just how significant passkeys are, it’s important to understand that they aren’t just an Apple thing–they’re about to be everywhere. Apple’s passkeys (which you’ll notice aren’t capitalized) are just its version of the passwordless secure authentication technology developed by the Fast Identity Online (FIDO) Alliance. FIDO is an association that works to minimize the world’s use of passwords, and which includes Google, Microsoft, and Amazon, among many other major players. And passkeys are built on the WebAuthn standard–an API FIDO helped write.
Google and Microsoft are rolling out their own passkeys and interoperability between platforms is one of the technology’s biggest selling points. So why is Apple getting all the headlines? As The Verge points out, “in order for the technology to succeed, it needs that marketing push.” And Apple is the acknowledged champion of hype-generation, so it makes sense for them to lead the charge.
Anatomy Of A Passkey: The Inner Workings
From an end user’s perspective, passkeys won’t feel particularly disruptive or revolutionary. When you create a new account on a passkey-enabled device, you’ll type a username and then authenticate with Touch ID, Face ID, or your device passcode, and…that’s it—on the surface. But a lot has changed behind the scenes.
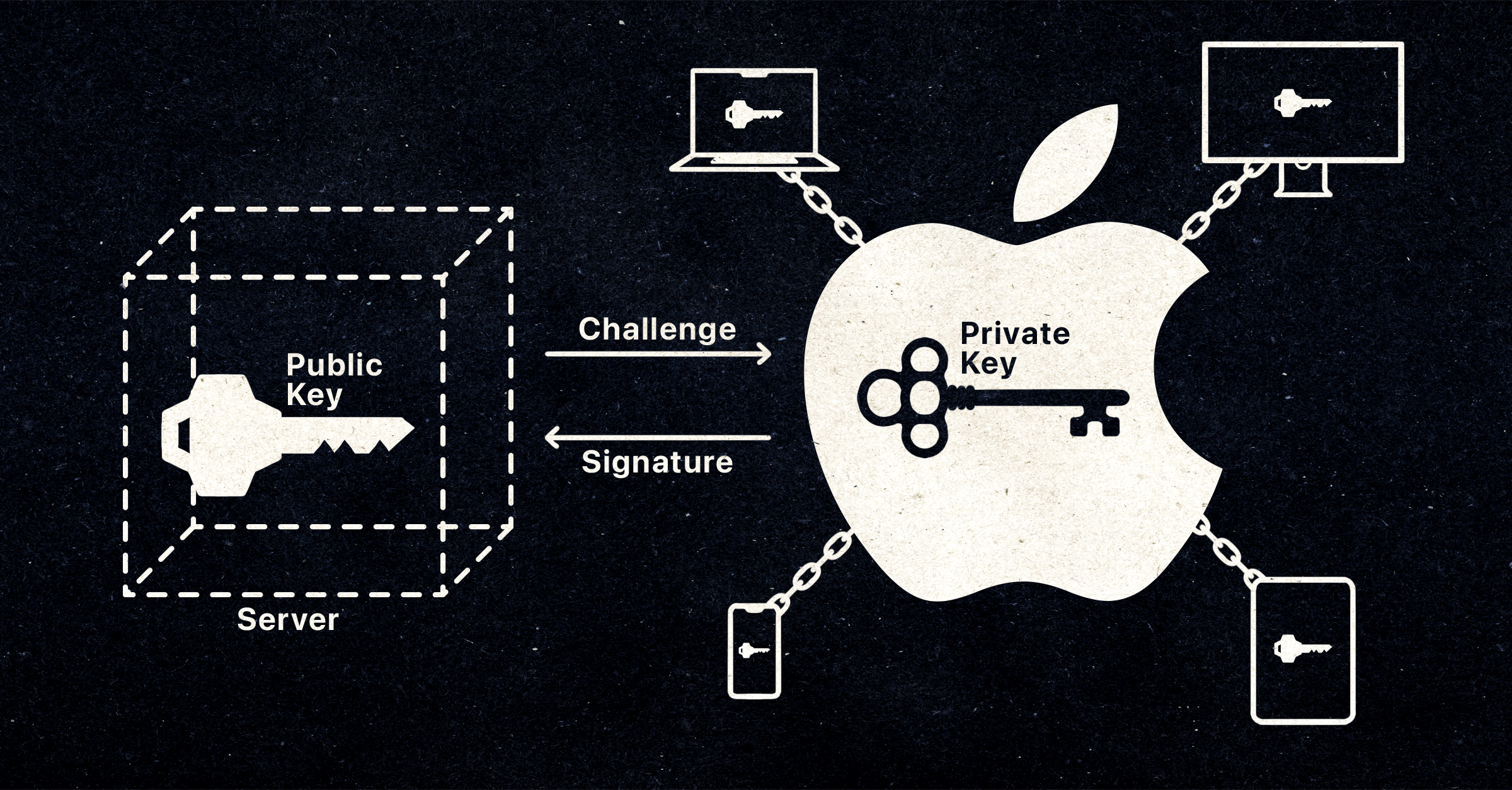
The primary difference between passkeys and passwords is how they share secrets. Passwords work by a user coming up with a string of characters, which an application then (theoretically) salts and hashes, and stores on a server.
By contrast, the WebAuthn standard works by generating a pair of unique and secure keys on your device. The public key is sent to and stored on the website or app’s server; the private key remains a secret that your device is responsible for protecting. When you return to a website or app to sign in, the server will generate a one-time challenge to prove that your device has the private key associated with the public key. Your device will accept the challenge, sign it using your private key, then send the signature back to the server for validation. Unlike the password, which is exposed every time you have to log in, the private key remains private.
The most familiar version of WebAuthn (up until now) stores keys on hardware dongles, which are highly secure but not great for usability or recoverability. Apple’s innovation is that after you create a passkey, it will be available across your Apple devices because it will be automatically saved to your iCloud Keychain. And since the Keychain is end-to-end encrypted and requires two-factor authentication by default, your private keys get to be both secure and accessible.
So we’ve established that passkeys are fundamentally different from passwords. What does that mean in practice?
Passkey Positives: Tougher Security, Kinder UX
Assuming passkeys are widely adopted, they could genuinely be a game changer in ending our current era of credential-based attacks. Credential stuffing would become much more difficult when passkeys simply don’t work for any website other than the one for which they were created. Servers would no longer have to guard passwords, and would therefore become much less appealing targets for hackers. And adding biometrics to the equation will seriously beef up multi-factor authentication (MFA), since the combo of something I know _and something I have_ is a lot easier to get around than something I have and something I am.
And what about the human advantages of passkeys? Authenticating with Face ID is certainly faster than typing out a password. And we can assume that users will be glad to be done with the experience of forgetting a password, jumping through multiple hoops to create a new one, and promptly forgetting that one too.
If this is the authentication of the future, as many headlines proclaim, I think it’s safe to say we’re moving in the right direction. But we’re not there yet, and for passkeys to succeed, they’ll still need to clear a few hurdles.
Passkey Pitfalls and Concerns
Apple observers have already raised a few objections to passkeys. Even though some of their worries are unfounded, their confusion is still impacting the perception of passkeys. And as Apple knows better than anyone, when it comes to technology succeeding or failing, perception is everything.
Cross-platform compatibility
When Apple first announced passkey technology at WWDC21, the ability (or inability) to use passkeys across platforms was an issue that called out on nearly every article comment, forum post, blog, and tweet.
What happens outside of the Apple ecosystem? For example logging into an account from an employer’s Windows machine or if (heaven forbid) a user leaves Apple’s world?
That’s a valid concern given Apple’s reputation as a walled garden, but there’s nothing to fear—as we’ve already mentioned, Microsoft and Google will implement their own, interoperable versions of the passkey. The workaround they’ve developed is a little convoluted, but it will allow you to access your credentials on devices that don’t support Keychain.
Let’s say you want to check your email on a friend’s PC: that device will generate a QR code. You’ll scan the QR code with your Apple device–proximity is key because the other device will send out a Bluetooth message with the information you need to sign in. Your Apple device will use the keys in the QR code to create an end-to-end encryption protocol that mimics the security of a passkey.
Recoverability
Apple cited recoverability as one of its major requirements for passkeys, so even those with a single Apple device are covered in the event they lose access to it. However, like their interoperability solution, the system for passkey recovery is a little complicated.
iCloud keychain escrow allows you to recover your passkeys if you meet certain conditions—one of which is the possession of your iCloud Security Key. Your account recovery contact can also help you regain access by verifying your identity. A recovery contact is someone close to you, like a trusted friend or family member, with an Apple device. Apple never learns who your recovery contacts are so it’s important that you remember so you can ask that person for your recovery code if you’re locked out. This, of course, depends upon you having set up an account recovery contact to begin with, and it’s far from clear that most people are doing this. Also, the human element here presents some risks of its own, since your recovery contact could keep you locked out of your data if your relationship turns sour.
Sharing
The potential messiness of combining data security and human relationships is also the subject of the other concern I saw echoed around the web.
The design is flawed. For example, my mortgage bank has given my wife and me one account. With a passkey, we would have to choose who has access. This example is not unique in any way, even though it doesn’t apply to the majority of accounts. Yet, these are very important accounts where passkey’s [sic] won’t be usable.
Variations on the above complaint were–and still are–common and show that Apple hasn’t done a great job marketing the usability of passkeys alongside the security. You can share passkeys, just like you share passwords. (That noise you hear is Netflix sighing in profound disappointment.) But there is a caveat: Passkeys can’t be pasted into an iMessage so they must be shared via AirDrop. The added security of proximity comes into play again here as Apple assumes you won’t initiate voluntary sharing of a passkey with a stranger. And the company has included other safeguards. For example, the ability to AirDrop a passkey will only be available to mutual contacts — you must have the receiver’s Apple ID in your contacts, and they need to have your Apple ID in theirs. Given this security measure, it would seem sharing is limited to other Apple users at the moment. So perhaps there are two caveats to passkey sharing.
The role of biometrics
There are other factors at play that Apple hasn’t addressed. But to be fair, these issues aren’t unique to Apple passkeys, but passkey technology in general. One such factor is the biometric component of passkeys and its potential for abuse.
Plenty of people have reservations about biometrics, including:
- What happens if they change? If someone’s fingers or face is disfigured in an accident, will they lose their credentials?
- What happens if your biometric credentials are stolen? The advantage of passwords is that if they’re compromised, they can be changed. But if someone figures out how to clone my fingerprint, I can’t go out and get a new one.
- Biometrics offer less protection from unlawful search and seizure and physical violence. Under current case law, the police can’t compel you to enter a password, but they can hold your phone up and let Face ID unlock your phone without your consent.
Even the most minor retention of data creates a very slippery slope, and near-constant surveillance is possible when large databases of biometric data are combined with other personal data points. The more we normalize using biometrics for everyday transactions, the closer we get to a world where there’s nowhere to hide, and that creates troubling potential for government abuse.
To their credit, Apple handles biometric data pretty securely (and we all know its stance on revealing user data). On top of that, folks with privacy concerns have the option to disable biometrics and use their device passcode for authorization instead. But forgoing Touch ID or Face ID means your device will only be protected by your passcode, and one could argue that means a passkey is no safer than a traditional password.
Passkey adoption
There’s also the issue of how to manage society’s transition to a post-password world–a challenge that can’t be addressed by Apple alone. Websites and apps will have to retain passwords for many years because it will be at least that long before there’s full adoption of passkey technology. If you create a passkey for your bank account, your bank can’t delete your stored password because it has no way to know that every single device you own (or will ever use to access your bank account) supports passkey technology. So the bank will keep your password on their server, where it’s always been.
Sure, websites could offer people the choice to delete their saved password when they create a passkey, but how many would opt to save the password just in case something goes wrong? And that will leave us about where we are now: vulnerable to attack because weak, reused and/or already-compromised passwords are stored in every corner of the internet.
Passkey Reality: The Impact
Users
Apple hasn’t announced plans to mandate users adopt passkeys, which means the technology will succeed or fail based on whether the general public chooses to embrace it. And there’s no way to know for sure that they will–we’ve discussed the added convenience and increased security, but they may not outweigh the issues the passkey needs to overcome to achieve full adoption.
Only time, and lots of it, will tell if users will have enough trust in the security of platform vendors to fully embrace passkeys as a replacement for passwords. And it’s possible this iteration of passkeys won’t even be around when that time comes. (After all, people have been talking about the “death of the password” for a long time, but it’s still alive and kicking.)
Passwordless authentication does appear to be the way of the future, whatever form it takes, so it’s probably best to embrace it now–but do it on your terms. If you don’t feel comfortable with biometrics, keep them disabled and use your device passcode instead.
Developers
While developers are the first people to tell you that passwords are outdated, that doesn’t mean they’re ready and able to make the switch to passkeys. (At least, not without a lot of work.)
Every app and website that requires a password will need an overhaul, which can mean hours learning new skills so the devs can implement the necessary changes and troubleshoot errors effectively. Again, it will be some time before every app and site across the web integrates passwordless technology and permanently removes its database of passwords. Even during the transition, devs will have to keep supporting older password-only tools, so there’ll likely be a long period where everyone will have to support both systems.
Passkey Review: The (Preliminary) Verdict
It will be interesting to see how Apple evolves passkey technology–and how it evolves with the technology. For example, will passkey implementation be required on the App Store? There are no plans for that so far, but given Apple’s recent history of mandating Sign in with Apple, it wouldn’t be surprising. And will user participation continue to be optional, or will the company make passkeys mandatory?
Passkeys might be the solution to the password problem but that problem has been part of our society for decades and won’t disappear in a few months–or years, for that matter.
Until then, you know the drill: use unique, complex, randomly-generated passwords; practice the principle of least privilege; and don’t break up with your password manager.





